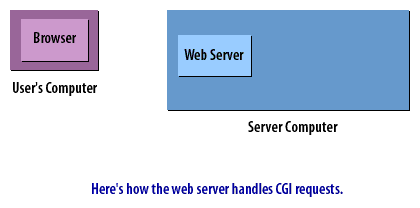
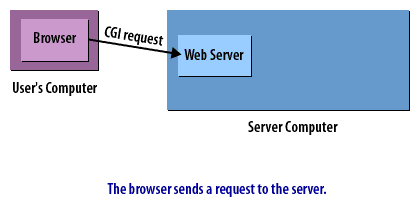
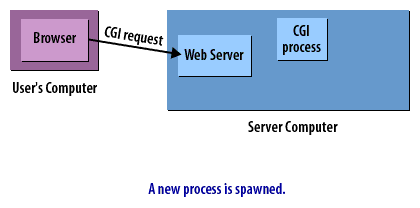
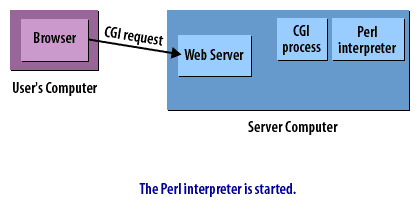
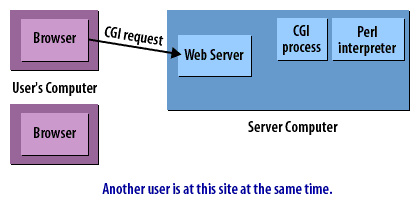
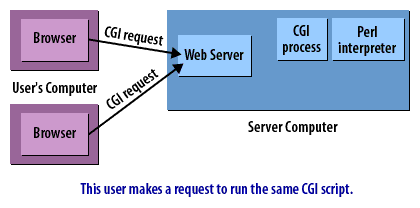
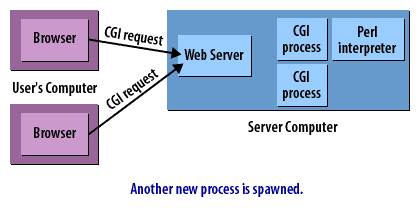
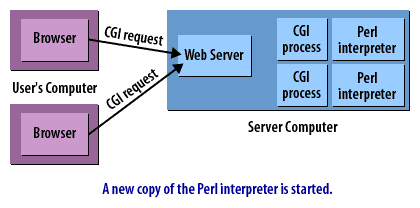
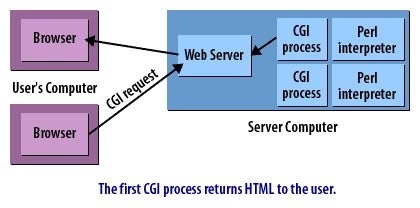
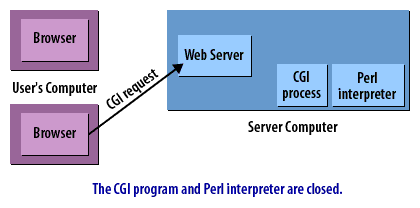
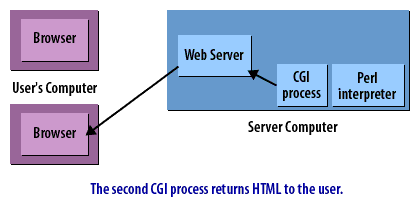
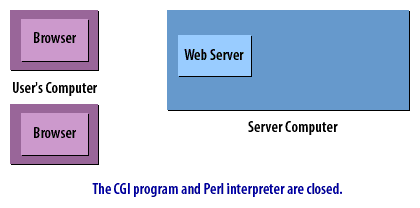
CGI Requests
Problem with CGI scripts
The problem with CGI scripts is that each one presents an opportunity for exploitable bugs.
CGI scripts should be written with care and attention since they are Internet servers or miniature servers.
Unfortunately, for many Web authors, CGI scripts are their first encounter with network programming. CGI scripts can present security holes in two ways:
Even if your server runs in a chroot directory, a incorrectly written CGI script can leak sufficient system information to compromise the host.
- They may intentionally or unintentionally leak information about the host system that will help hackers break in.
- Scripts that process remote user input, such as the contents of a form or a "searchable index" command, may be vulnerable to attacks in which the remote user tricks them into executing commands.
Even if your server runs in a chroot directory, a incorrectly written CGI script can leak sufficient system information to compromise the host.
Java Servlets